In cybersecurity, organizations have several options for assessing their security posture. Among the most common are vulnerability scanning, penetration testing, and red teaming. While these terms are sometimes used interchangeably, they differ significantly in approach, objectives, complexity, and cost.
Knowing which assessment type fits best for your organization can save resources and ultimately improve your defenses more effectively. Let’s break down these differences and help you decide which is right for your company based on your security maturity.
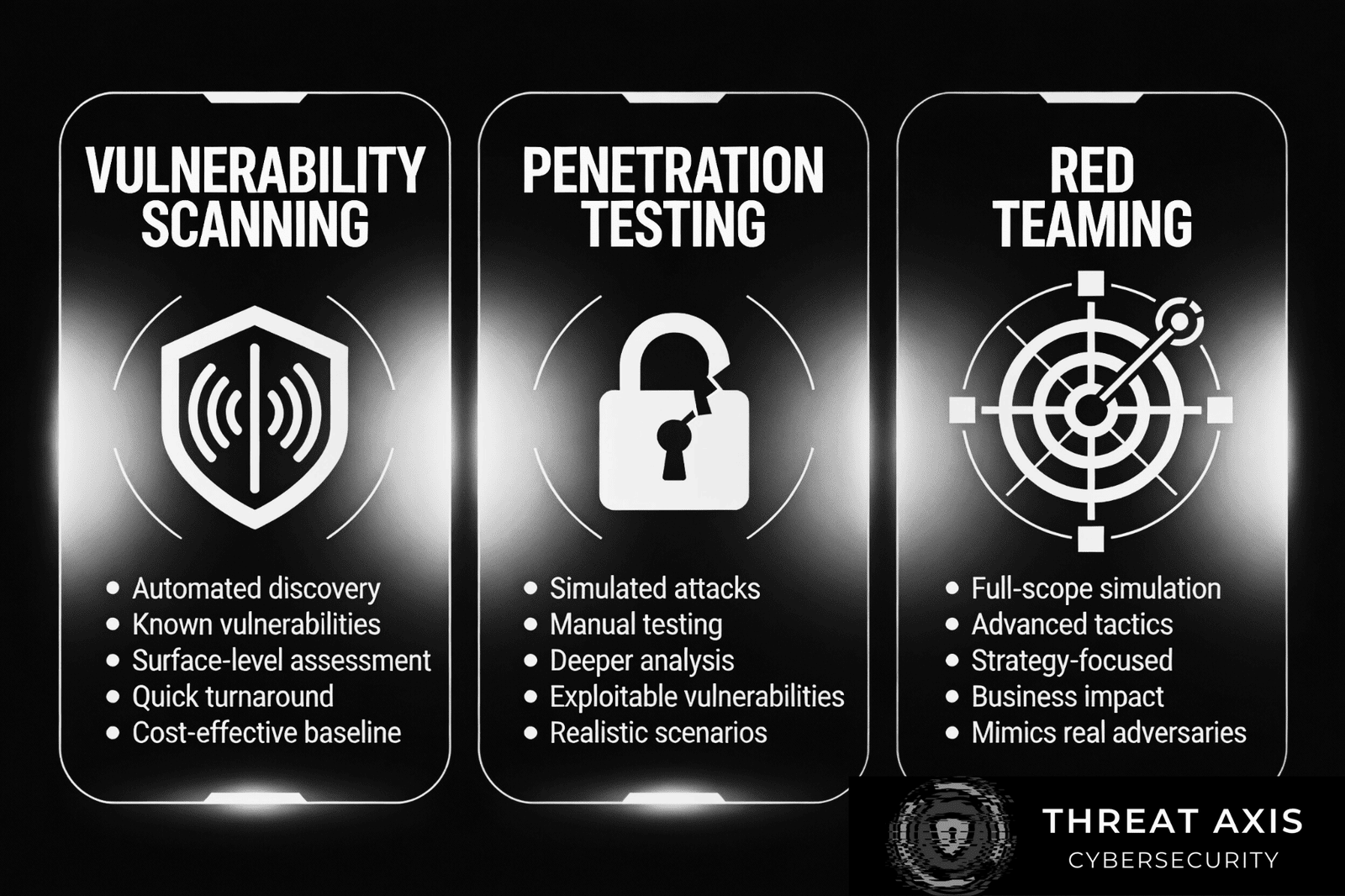
Vulnerability Scanning: The Automated Security Health Check
Vulnerability scanning is like going for your routine checkup. It uses automated tools to scan systems, networks, and applications for known weaknesses — missing patches, open ports, insecure configurations, and more. These scanners generate reports highlighting potential risks with severity levels.
Because it’s automated, it’s quick, cost-effective, and easy to run regularly. But remember, it only points out “red flags” — it doesn’t dig deeper to see if flaws can be exploited or what damage could actually happen.
Vulnerability scanning is ideal for startups and small-to-medium businesses looking to maintain basic cyber hygiene and identify obvious problems early.
Penetration Testing: Ethical Hackers in Action
If vulnerability scanning is a checkup, penetration testing is a stress test. Skilled security professionals try to simulate real attacks by actively exploiting vulnerabilities to understand the risks in a practical, hands-on way. These tests help validate defenses, prioritize fixes, and provide proof-of-concept exploit evidence.
Penetration tests are more targeted and in-depth than scans, often spanning days or weeks. They require human expertise, making them pricier but invaluable for organizations needing compliance validation or wanting a realistic perspective on their security effectiveness.
Medium-maturity organizations — those with fundamental security controls in place — benefit most from penetration testing, as it helps identify hidden weaknesses and evaluate incident response readiness.
Red Teaming: The Full-Spectrum Adversary Simulation
Red teaming takes security testing to another level. It’s a multi-layered simulation that mimics how sophisticated adversaries target people, processes, and technology using a blend of social engineering, physical infiltration, and cyber attacks.
Unlike penetration testing, red teams have broad freedom to achieve complex objectives over extended periods, often going undetected by internal teams. The goal is to test not just technical defenses but also detection, response capabilities, and overall organizational resilience.
Red teaming demands mature security programs, committed leadership, and a willingness to uncover uncomfortable truths about the organization’s security posture. It’s best suited for large enterprises and critical infrastructure organizations ready for realistic, adversary-style challenges.
How Do These Approaches Compare?
| Aspect | Vulnerability Scanning | Penetration Testing | Red Teaming | |
|---|---|---|---|---|
| Purpose | Identify known vulnerabilities automatically | Exploit vulnerabilities to assess risk | Simulate advanced adversaries against all defenses | |
| Scope | Broad, shallow, frequent | Targeted, in-depth | Comprehensive, multi-vector | |
| Method | Automated tools | Skilled manual testing | Goal-oriented, stealthy operations | |
| Duration | Hours to days | Days to weeks | Weeks to months | |
| Cost | Low | Medium | High | |
| Output | Vulnerability list with severity | Exploited vulnerabilities with proof | Operational impact, detection gaps | |
| Security Maturity Fit | Early-stage SMBs, limited cybersecurity | Moderate maturity, compliance focus | Mature programs with advanced defenses | |
| Ideal For | Identifying areas for patching and hardening | Validating security controls and response | Testing overall organizational resilience |
Which One Should Your Organization Choose?
If you are early in your security journey or have limited resources, vulnerability scanning should be your starting point. It keeps you aware of obvious problems and assists with routine hygiene.
As you grow and implement controls, it’s critical to understand if your defenses hold up under realistic attack conditions. That’s where penetration testing shines — it uncovers hidden weaknesses and tests response effectiveness.
When your security program matures, and you want to prepare for real-world threat actors targeting your environment, red teaming provides a rigorous, adversary-emulation experience that hones detection, response, and recovery across your entire organization.
Choosing the right approach depends on your organization’s current security posture, risk tolerance, and budget. Applying these methods sequentially as you mature your defenses ensures you continuously strengthen your cyber resilience.
Understanding these differences empowers you to invest wisely and protect your assets effectively.
If you want to dive deeper into these security assessments or need help determining which is right for your business, reach out
